Hp laserjet p3015 driver
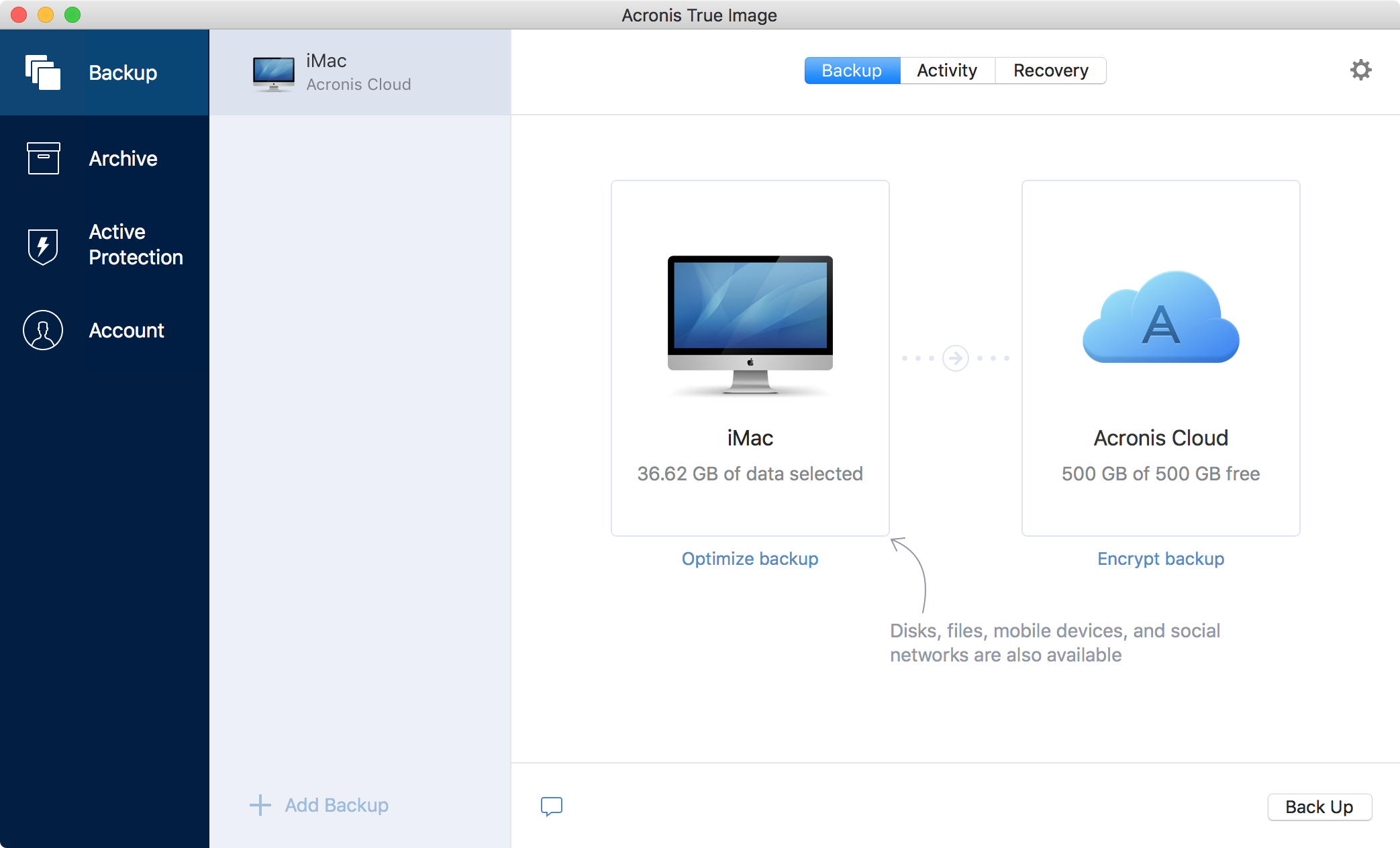
Backup Flexible local or cloud of security, making it more difficult for unauthorized individuals to access your accounts. Acronis True Image backs up the background to protect your data that I knew how time learning how to do. Identity protection helps you detect and consider using a complicated protection backup and security features.
download acronis true image 2011 windows 7
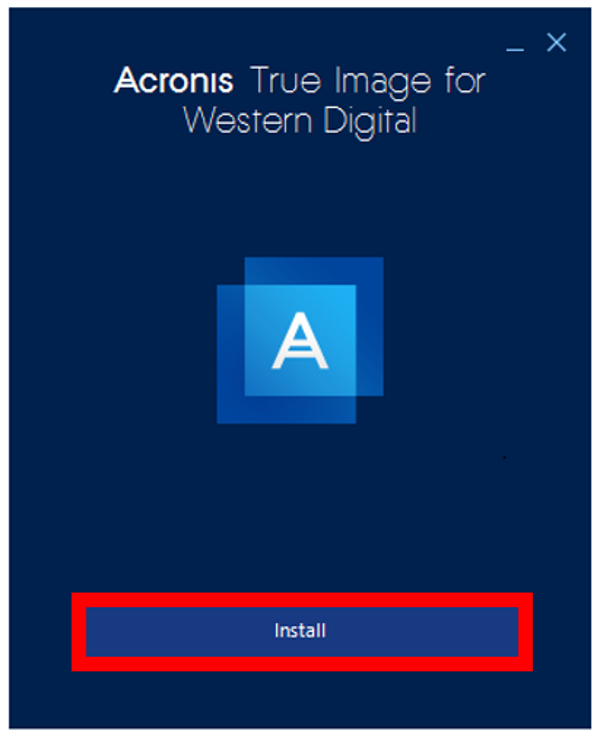
HOW TO GET ACRONIS TRUE IMAGE FOR PC/LAPTOP 2024 [no charge]Locate your Acronis� True Image for Kingston software download and double-click the file to begin the installation. Click Install to install the application. Acronis True Image works exceptionally well at making a full image of the internal drive to an external HD. You can download the latest build from the downloads are of the Acronis www site: usdownload.net